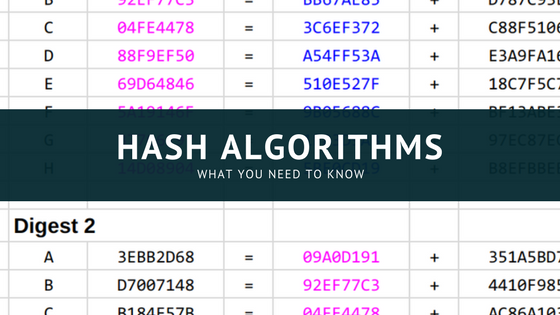
How Cryptographic Hash Functions Solve a Very Difficult and Important Problem | by Bennett Garner | Medium

Sapna💫 on Twitter: "Hash-transactions are taken as an input and run through a hashing algorithm (Bitcoin uses SHA-256), gives an output of a fixed length. #Cryptocurrency #TheFutureOfFinancelsHere #Blockchain… https://t.co/XH5hbsBsg7"
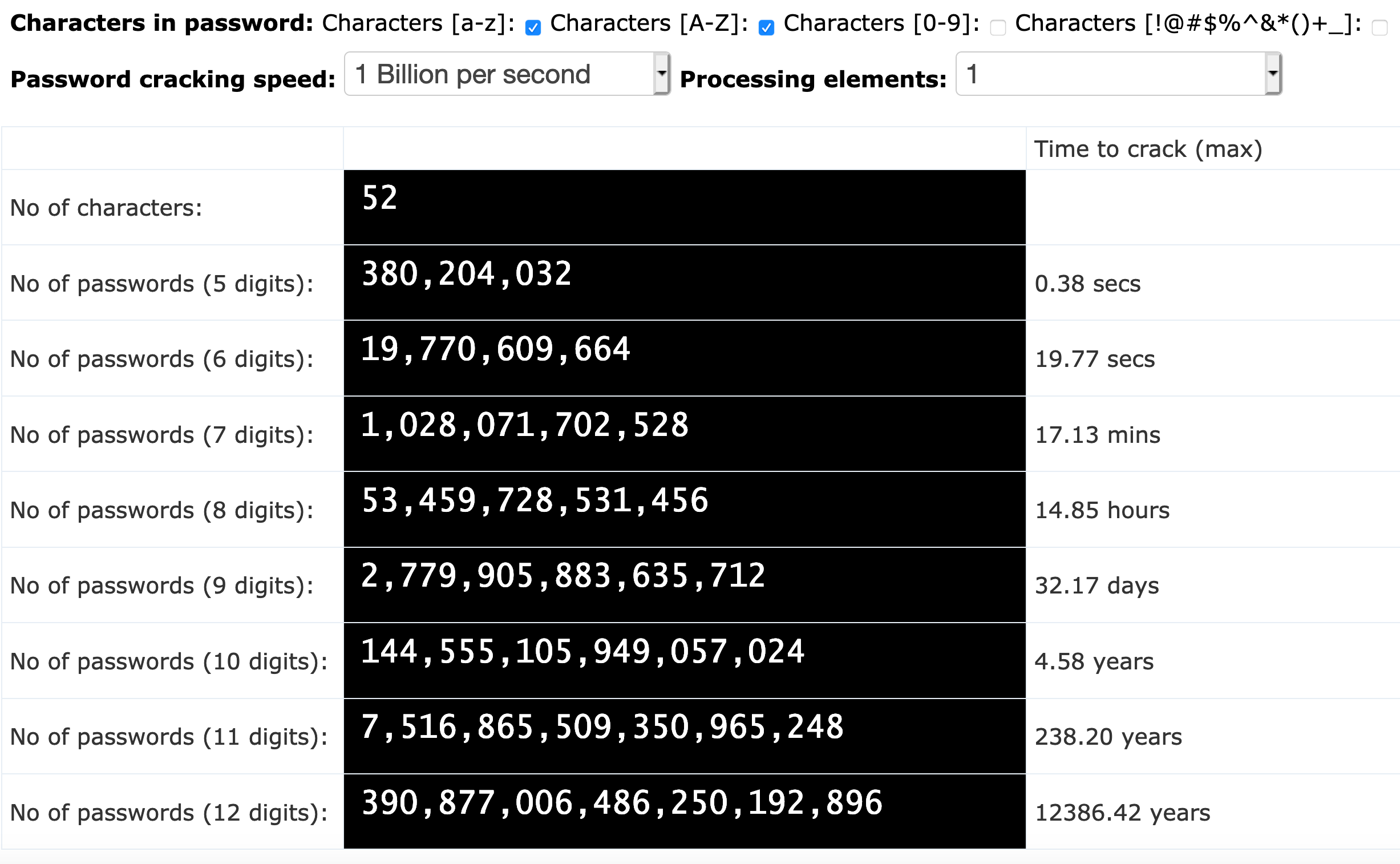
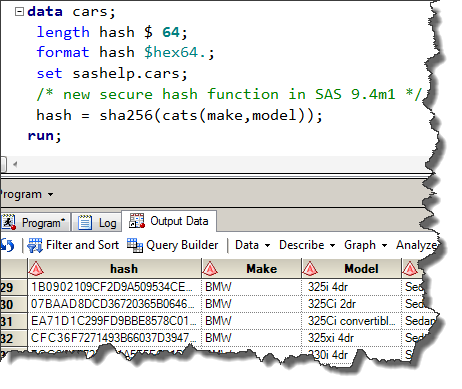
The Problem With Passwords…. A couple of comments I received… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium



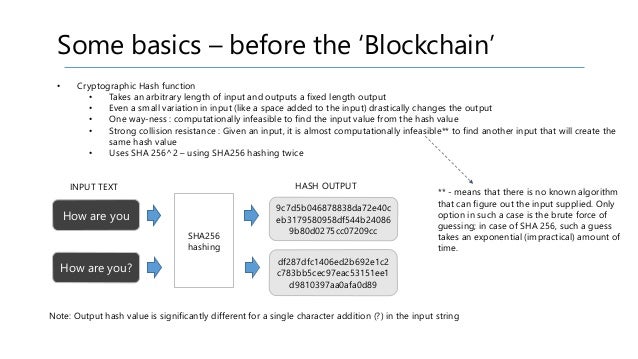












![What Is Cryptographic Hash? [a Beginner's Guide] What Is Cryptographic Hash? [a Beginner's Guide]](https://techjury.net/wp-content/uploads/2020/06/different-hash-with-alterations.png)
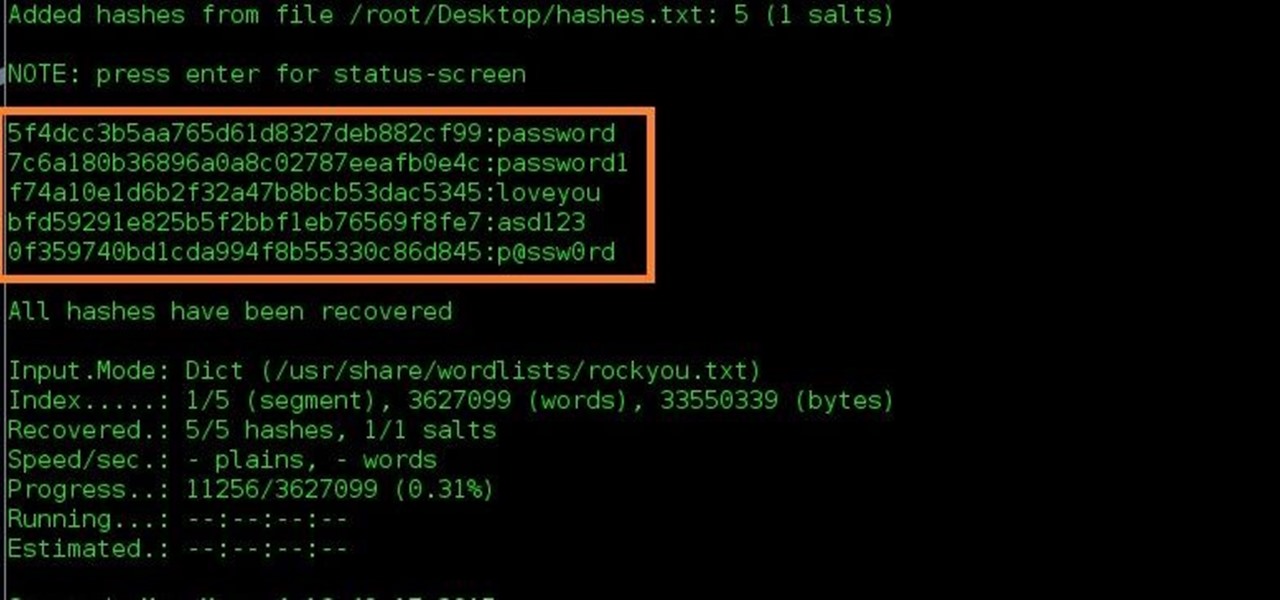
![What Is Hashing? [Step-by-Step Guide-Under Hood Of Blockchain] What Is Hashing? [Step-by-Step Guide-Under Hood Of Blockchain]](https://i.ytimg.com/vi/IGSB9zoSx70/maxresdefault.jpg)
